Considerations for effective and efficient security camera design

By Keith D’Sa
Design/construction professionals have countless considerations to manage when driving a new building project. As a result, video surveillance systems can sometimes become an afterthought. However, as with all infrastructure components, making the right decisions in the early stages of the project’s development can save both time and complications later.
The first choice that needs to be made is between analog and Internet protocol (IP) video, with the latter increasingly being specified for projects.1
The differences between the two are similar to any analog versus digital technology comparison. With digital technology, the end-user enjoys vastly improved image quality, a better total cost of ownership, and increased functionality.
Technically speaking, analog video employs a signal from an analog camera transmitted over a coaxial cable (e.g. RG-59U or RG-6U), whereas IP video is a digital signal transmitted as data over an Ethernet cable. On top of the functionality and resolution limitations, analog systems offer limited surveillance applications because the signal is sent point-to-point, while IP video can be streamed to multiple points on the network.

Additionally, analog uses interlaced video (i.e. two fields overlaid into a frame) that produces a lined effect on the screen and increases the chance of motion blur appearing on fast-moving objects, while IP’s progressive-scan mechanism does not overlay two images, minimizing this problem. Lastly, it is important to note IP is more scalable—or expandable—than analog. The number of analog cameras that can be used is tied to the number of ports available on the digital video recorder (DVR). That means, for example, a customer with a 16-port DVR and 16 cameras installed would have to buy a new DVR in order to add one more camera. Network video, by comparison, can scale from one camera to 17 to 1000, or any number.
Planning a new security system around the following nine considerations will help provide an efficient and effective security design.
1. Detection vs. recognition vs. identification
Deciding what a project needs from each camera is an important consideration affecting the system design. The criteria to weigh are detection, recognition, and identification.
‘Detection’ simply means the camera detects someone or something has entered its field of view. If this is all the end-user requires, then a standard-definition camera would suffice. Thermal cameras, which have dropped significantly in price over the years from tens of thousands of dollars to less than $3000 each, provide another detection option, especially in remote applications such as parking lots or construction sites.
‘Recognition’ delivers a slightly higher level of assurance, essentially allowing a person, object, or animal to be distinguished based on characteristics. For example, if a building’s regular employee is tall and always wears a blue jacket, personnel can be fairly certain that when video shows a tall person wearing a blue jacket, it is probably said employee.
‘Identification’ is the highest level of assurance, because the image is of sufficient quality to positively identify a person. This requires a certain resolution (i.e. pixel count). A good guideline is a minimum of 80 pixels across the face to sufficiently identify an individual. Security vendors provide tools for planners and integrators to measure the number of pixels generated in a real-world scenario. This means installed cameras can be checked to ensure they are delivering ID-quality images.
The distinction between identification and recognition equipment rests on resolution and camera placement, with the two types typically working together to cover a building or outdoor area. For example, a convenience store would place eye-level cameras at the doors and overview cameras elsewhere. In the case of a suspected shoplifter, the overview cameras would show a general picture, while the eye-level camera near the door would produce a clear identification image.
2. Beware of the dark…and the light
Video quality starts with light quality. Since light activates the pixels that create the images, there should be planning to ensure sufficient lighting to generate clear video images. When this is impossible, low-light cameras, thermal cameras, or infrared illumination can be employed.

Conversely, too much light can be equally difficult to manage. Building entrances can present particular challenges for video systems. For example, on sunny days, a bank’s customers stroll from glaring sunlight into relatively subdued indoor lighting. The light pouring in throws off the exposure of the camera pointing at the door. As a result, the people in those identification shots end up as backlit silhouettes—almost useless if bank personnel or law enforcement need a clear image to identify.
However, installing a wide-dynamic-range (WDR) camera will deliver a picture with both faces and the surrounding exterior properly exposed. Advanced WDR cameras capture two or more full-frame snapshots of the scene at different exposures—some overexposed, some underexposed, and some in the middle. The processing power in the IP camera helps seamlessly combine these images to eliminate the too-dark and too-bright zones, and then presents a consistent, smooth video to the viewer.
It is important to note this capability is not available on every camera. Most cameras, even high-quality ones, are not designed for wide dynamic range. This means specifiers must select these cameras at planning time.
Without that foresight, management personnel moving into new buildings may discover they cannot make out detail on people walking in the door, or of cars driving into a parking garage. Lighting is often overlooked, and it is not uncommon for security vendors to be called in to replace standard-issue units with WDR models.
3. Manage network requirements
Since IP cameras transmit video as data, they create network traffic. However, with proper planning, camera selection, and configuration, the video bandwidth should be completely manageable.
One issue is camera-users are often drawn to the implied promise of products with high megapixel (MP) counts. Simply put, bigger is not always better in surveillance—image usability is what matters.

First, most installations simply do not require massive resolution. Many 1.3-MP network cameras produce HDTV 720p video, while 2-MP units deliver HDTV 1080p images—quality sufficient for most applications. Conversely, blanketing a building with 5-MP cameras could create bandwidth problems.
Whether the end-user needs to detect, recognize, or identify people or objects affects how many pixels per foot the camera needs to produce. In a smaller room, lobby, or hallway, sometimes even basic super-video-graphics-array (SVGA) resolution will deliver the necessary quality.
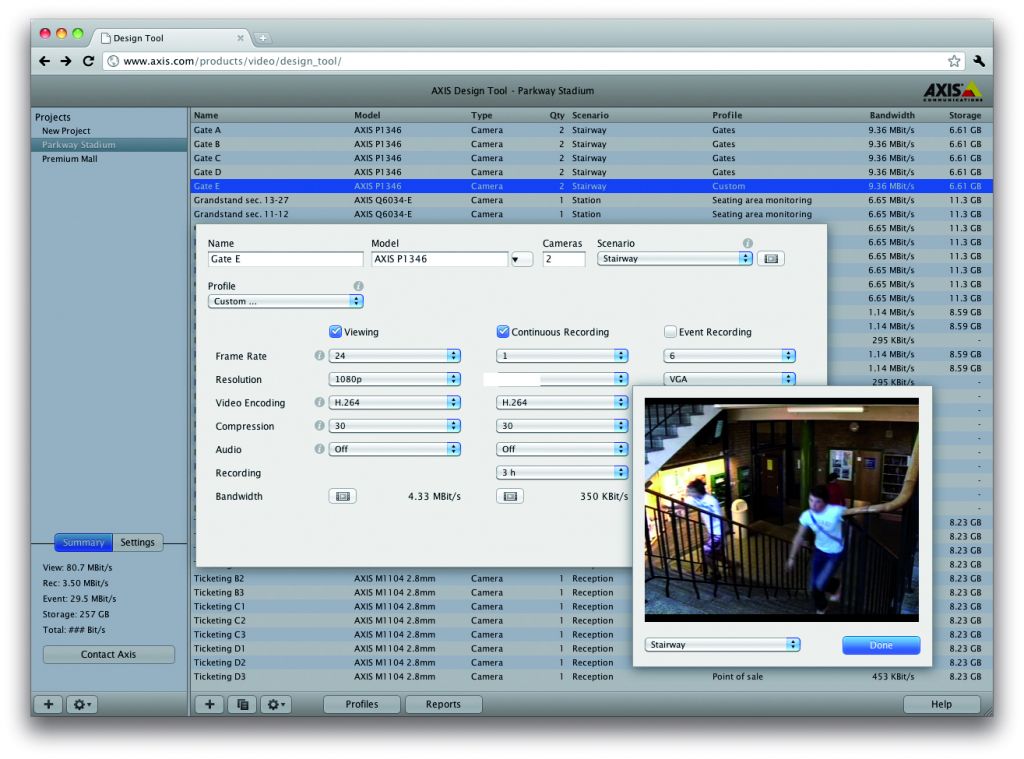
How the camera handles light, darkness, and movement also affects the bandwidth stream. Many manufacturers offer calculation tools estimating the bandwidth load from a camera based on factors such as frame rate, resolution, compression, and movement.
The resolution required in each area of a building must be determined, and then a network needs to be planned to handle the load. A modern and well-designed network should suffice if configuration is properly planned.
The edge devices of an IP video system—cameras, monitors, and some storage devices—are installed after the drywall and paint is applied, however, the system layout and camera placement is decided prior to breaking ground to accommodate cable runs, network drops, and lighting considerations.
Also, the number of remote users must be determined. Here, unicast and multicast come into play. In the former, the sender and the recipient communicate on a point-to-point basis. If a camera produces a data-stream of 100 MBps, one viewer will consume 100 MBps of network capacity, while five viewers (e.g. security guards) will consume a total of 500 MBps. By contrast, the more sophisticated multicast systems use network routers to manage the data, essentially allowing cameras to broadcast one signal to multiple users. Those five simultaneous users would require only 100 MBps in a multicast environment.
Planning a security infrastructure employing appropriate resolution on each camera and operating in a multicast configuration will keep the network load to a manageable level, and ensure the security system does not interfere with business-critical network processes.
4. Plan retention and storage capacity
Captured video content must also be stored. There are three main factors to consider when determining how much storage an implementation requires:
- how much video does the client want to keep;
- what resolution is required; and
- how will the content be recorded.
Clearly, increasing the amount of video to be stored—from two weeks, to two months, to two years—will increase the required storage capacity. Similarly, high-resolution video consumes more space than medium- or low-resolution content.
For example, in an implementation requiring only one frame per second with fairly low resolution, six-months of storage capacity is inexpensive and easy to manage. However, if the same client expects 720p resolution at 30 frames per second, the resulting costs and complexity significantly increase.

It is also important to tune the type of video recording to the setting. For example, many shopping malls are open for business approximately 11 hours on weekdays, and eight hours on weekends. The rest of the time, there are no occupants aside from security guards. Continuous high-resolution recording during closed hours needlessly fills up storage space.
Also, in a shopping mall, a designer and systems integrator will employ IP cameras with motion detection capabilities. When the building is closed, they begin recording only when there is motion, so a thief breaking in will be caught by the system, but hours of empty corridors will go unrecorded. Nevertheless, a live stream is always accessible.
The process of motion detection can be performed at the camera or by the centralized video management software (VMS) system. The advantage of camera-based detection is it also reduces network load, as the camera only transmits back to the server when motion triggers recording.
A variation on this system is often used in environments in which it is advantageous to have a constant record. Hospitals, for example, may record at a low frame rate and low resolution (i.e. one or two frames per second at SVGA quality) until the camera detects motion, at which point the camera is triggered to send video at 30 frames per second in HDTV quality.
5. Look for integration capability
The specified equipment should be able to interface with other assemblies, such as access control, intrusion, building automation, fire, or intercom systems.Ideally, specifiers and integrators will understand the long-term growth strategies of the end-user. Clients may not immediately desire an access control system, but if the need eventually arises, they will not want to rip out the existing system to get that integration. There are a surprising number of VMS packages that do not support access control. Selecting a system only offering limited integration options could be an expensive decision later.
Additionally, design tools are often able to simulate equipment from some manufacturers. Professionals who use computer-aided design (CAD) of building information modelling (BIM) software ‘place’ camera types (even specific models) into their designs to assess how they will look and perform in the real world.
6. Measure the distances
There is a common myth IP cameras cannot be installed more than 100 m (328 ft) from a network switch or router at the end of its service life. This myth originated from the Institute of Electrical and Electronics Engineers (IEEE) 802.3af standard, which states twisted pair copper wiring has this distance limitation. It is recommended the last run of cable not exceed 100 m, but there are certainly technologies that can extend the distance beyond this standard, namely local area network (LAN) extenders, power over Ethernet (PoE) repeaters, fibre optics, and wireless technology.
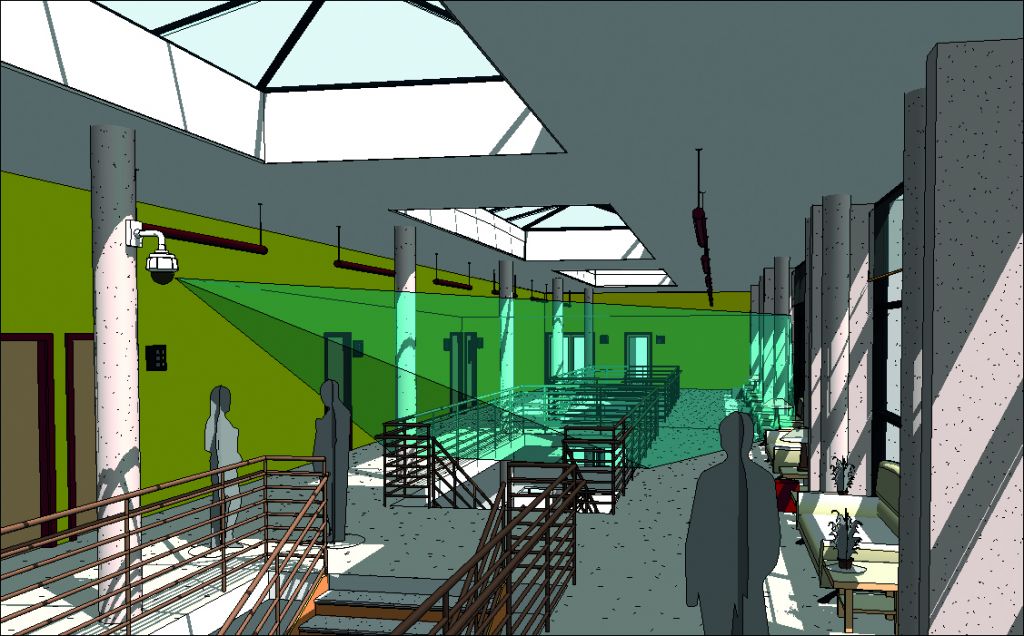
Knowing this is important because cameras require both cabling and power, so accommodations must be made at construction time if long cable runs are required to connect cameras. While distance-boosting devices exist, they can add additional cost to the installation. The design goal is to place switches strategically so few, if any, boosters are required. This strategy is employed in many large home-improvement retailers, which operate in big warehouse-like spaces.
One retailer (with whom this author’s firm has worked) installed intermediate distribution frame (IDF) cabinets along the cable runs to bridge the distance between the cameras and the VMS server. This was more cost-effective than using PoE repeaters because switches in the cabinets have multiple ports and therefore can handle multiple cameras, whereas repeaters would have to be added to each cable run. Cable run lengths are one design element that is often overlooked—it can be an expensive omission.
7. Consider the property’s operational uses
Building use and occupant types should both factor into the initial design process. Considering traffic flow and hours of operation are different for each building type.
For example, covering the entrances of a recreation centre tends to be more important than in other projects. This is because the high traffic volume may result in higher incidences of slip-and-falls, especially when it is raining or snowing. In a warehouse setting, one large courier company designed its video security system on the premise security concerns would originate from outside the building. After 10 years of operation, it learned employee theft was a significant problem, and it had no cameras placed to deter this misbehaviour. Additional cameras had to be added, and the employees were made aware of the new security measures.
In that case, a knowledgeable designer could have performed double duty—not only as a loss prevention expert, but also advising employee areas that require security coverage.
8. Plan for future use
One of the best favours architects and planners can do for clients is to create an adaptable system that can grow as client needs change. Using open IP technology is essential for future planning.
Sometimes planning for the future means turning down what appears to be a good deal (e.g. cameras with seemingly impressive specs and a good price) because the systems are built on closed proprietary technologies, so functionality cannot be added later.
For example, if a system is originally put in place for loss prevention, and a few years later the company wants to use cameras for heat mapping (i.e. determining patterns of movement through the building), there would be disappointment when building owners learn the originally installed cameras are incompatible with the necessary analytics.
Instead, cameras accepting new applications should be specified. The hardware comes with a set of capabilities out of the box, but its ultimate use is limited only by the imagination of software developers. This means functionality such as heat-mapping, occupant counting, and licence plate recognition can be added.
Specifically, look for equipment conforming to the Open Network Video Interface Forum (ONVIF) standard. ONVIF was formed in 2008 to create and administer a standard for video surveillance cameras and other security devices that ensures interoperability regardless of manufacturer.
9. Select a certified integrator
Onsite installation errors can impact even a thorough and professional plan. For example, about a decade ago, a company this author worked with moved into a new building, and the security system installers placed a camera directly in front of a motion detector, rendering it useless. Such issues are not always apparent on paper but a properly trained security integrator will catch these concerns immediately and find a solution.
To ensure there are benefits from that type of expertise, partnering with integrators who are trained and industry certified is recommended. Many manufacturers have their own product certifications, but the certifications holding the most credence are those proctored by a third-party that covers issues such as network design, bandwidth, resolution, and general best practices.
Conclusion
For design professionals incorporating IP security systems into their projects, an ounce of security planning will often save a pound of costly renovations. The most efficient and cost-effective time to make fundamental infrastructure decisions is at the design stage, so architects, specifiers, and designers can incorporate security best practices early in the planning and construction process to save time and money while helping plan for future system needs.
Notes
1 For example, electronic market research firm, IMS Research, predicts revenues from network video products will overtake analog this year, according to the report, The World Market for CCTV and Video Surveillance Equipment. (back to top)
Keith D’Sa manages Axis Communications’ national accounts and architect and engineer programs in Canada. He brings 12 years of hands-on experience designing both analog and IP Video, Access Control, and Intrusion System. Prior to joining Axis Communications, D’Sa held national positions at GE Security, UTC Fire & Security, and ADI (Honeywell). He can be reached by e-mail at keith.dsa@axis.com.







